Our Technology Partners














Cybersecurity Layers


PERIMETER LAYER ( Firewalls )
It is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. A firewall can be hardware, software, or both


NETWORK LAYER
the concern here is who and what devices can access your system. But, the bigger part of the network layer is what people and devices can access once they’re inside your system.


ENDPOINT LAYER
Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns.


APPLICATION LAYER
Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked.


Data Layer
Data security is the practice of protecting digital information from unauthorized access, corruption, or theft throughout its entire lifecycle.


HUMAN LAYER
90 percent of data breaches are caused by human error & social engineering attacks which target customers’ employees
Our Cybersecurity Solutions
Internal Network Access Protection
Prevent Un-authorized Users from accessing your Network
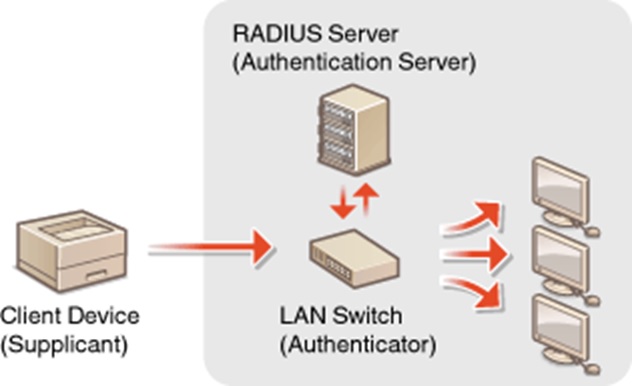

801.1x Authentication
Any User try to access the Network through wired or Wireless media , the Authenticator ( Switch / Access point ) will authenticate this user in a corporate with Authentication Server to determine if this user is allowed to access or will be prohibited
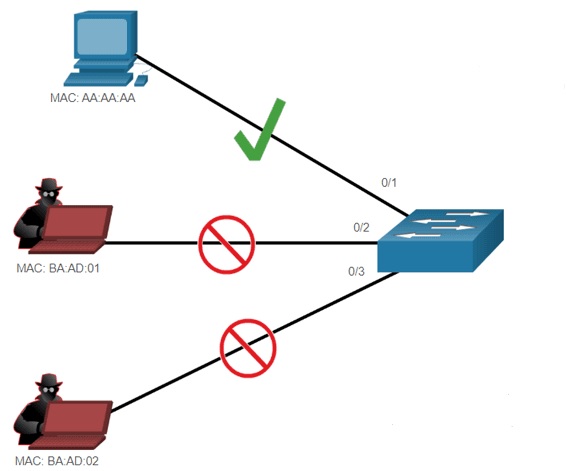

Port Security
a safe guard will be placed on the Switch port to allow only the authorized mac address to access the Network , any un-authorized Mac Address try to be connected will be prohibited or blocked .
Wireless Guest Access Management
2FA Web-based Access Control
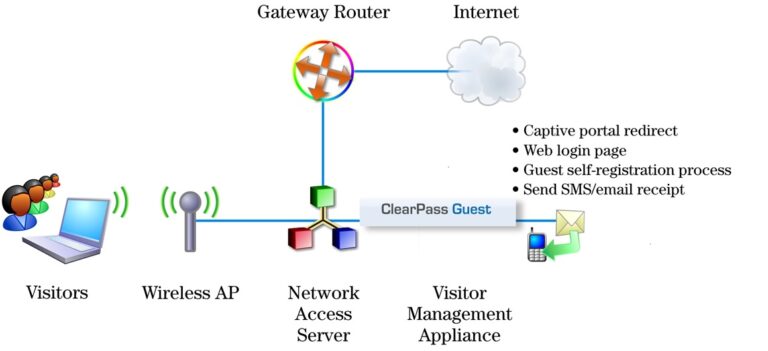

Captive Portal Authentication
Captive Portal two-Factor Authentication for Wireless Guests then putting them in a separate Guest VLAN then assign the allowed resources to be accessed ( Network Printers , Internet , …etc )
UTM Firewall
Multiple Security Features / Services in one Device
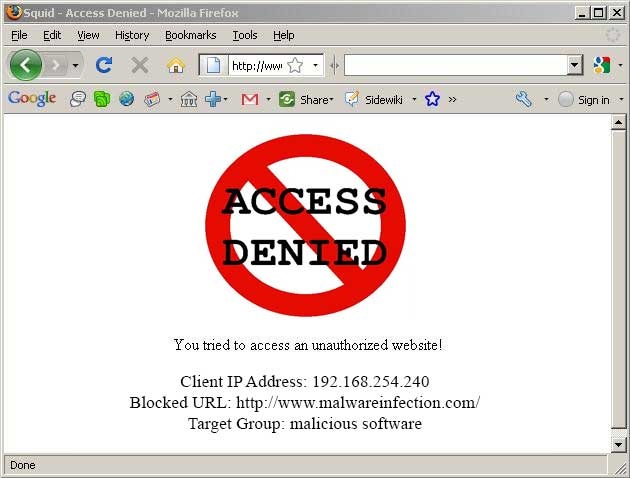

Web Filtering
Allow Or Deny Websites Accessing
Block Some Websites for some users in a specific time or forever so , you can keep your organization internet services from being abused
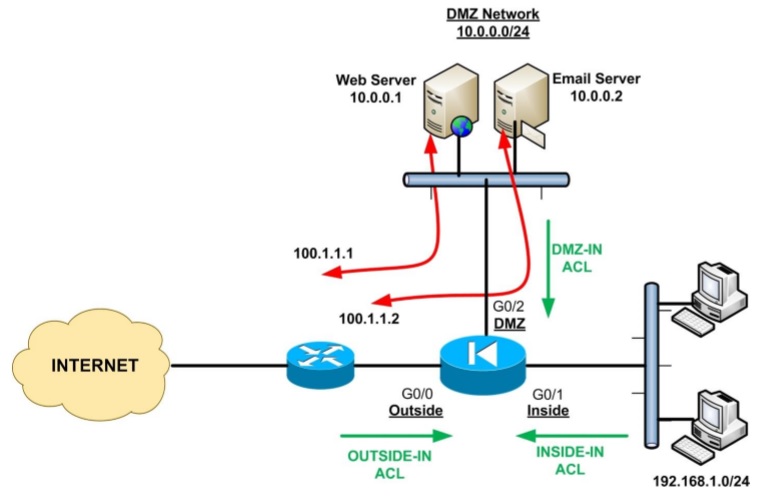

Secure App Publishing
By using static NAT with Deep inspection
You can safely publish any internal Server on the internet using Static NAT in addition to adding deep inspection for any traffic coming from internet to the Published Server(s)


Intrusion Prevention
Prevent Malicious Traffic
Detect and prevent any Malicious Traffic from accessing the Network


Anti-Spam
Detect and prevent Spam Emails
the Anti spam Filter engine used to detect & prevent the unsolicited or malicious Email message


Application Control
Permit or deny internet Access for Application
Block the internet access for your internal user Applications such as Facebook , YouTube , Messenger , …etc


Anti-virus
Detect and prevent Viruses Traffic
The internal antivirus scan engine supports scanning for specific Application Layer transactions allowing you to select the content (HTTP, FTP, SMTP, POP3, or IMAP traffic) to scan.
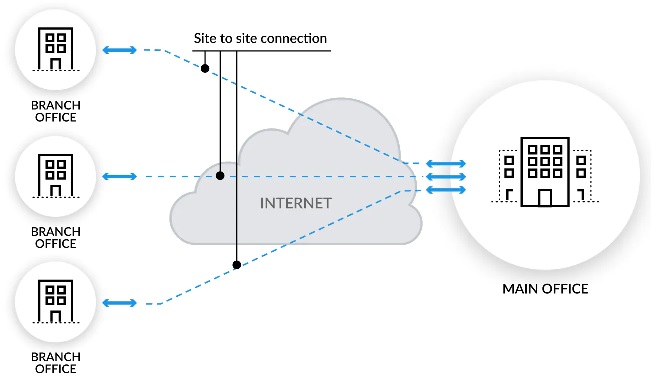

S2S VPN
Site to Site VPN
Connect all Remote Branches with HQ with high Secure , Fast & reliable VPN Tunnels
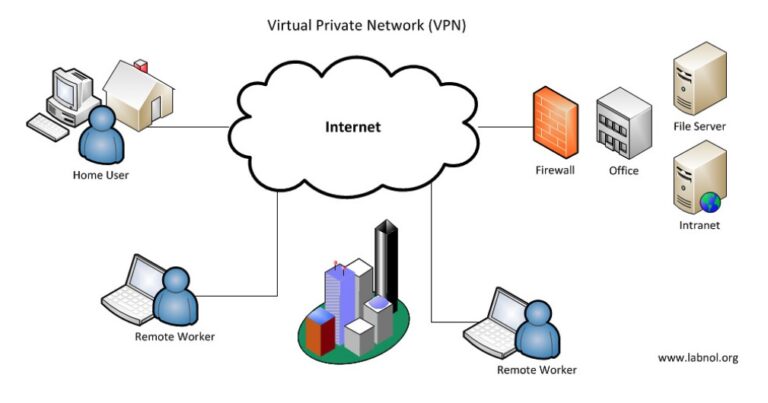

Dialup VPN
Point to Site VPN
The Remote User Can securely access the corporate resources from anywhere , anytime


What is Structured Cabling System ?
it is organized Network Cabling Solutions that provide you with much easier facility for managing your cabling & fixing the cabling issues in a very short time.
Our Professional Services
Design
According to the Customer’s Applications and Services used over the Network in addition to the Nodes Distribution & distances putting into consideration any Future Expandability , we start put the best fit design to the Cabling System .
Supply
Supply all Cabling System components including Cable Rolls , Cabinets , Patch Panel , Cable Organizers , Modules , Patch Cords , Faceplate , Pipes & Tray .
Implement
Start the implementation phase according top the predefined one in the Project plan . we put the Quality & time of executing the task as a higher priory concern
Termination
start terminating the Cables from Both sides according to the Standard in addition to putting the Labels on Cable , Faceplates & Patch panel
Testing
Fluke Testing for the entire cabling System to discover any issues with the System ( Attenuation , Insertion loss . tension , Improper termination , …etc )
Documentation
Complete Port-Location Mapping sheet to be used in VLAN Configuration and for any Tracking in addition to AS -Built Drawings for the Entire Cabling System showing the Cable Paths & Node distribution
Our Security Solutions Projects


ZAOASIS FACTORY
-Network Access Protection
-Server Hardening
-Guest Access Control
-Perimeter Security
HANA WATER
-MPLS to IPVPN Migration
-Configuring Symantec EPP
-Network Access Protection
-Perimeter Security


ARTIC CO.
-MPLS to IPVPN Migration
-Network Access Protection
-DMZ Implementation
-Perimeter Security


BAZY
-MPLS to IPVPN Migration
-KASPERSKY EPP
-Network Access Protection
-Perimeter Security


GOLDEN BR RECRUITMENT
-IPVPN 10 Branches
-OpenVPN ( IP Telephony )
-Perimeter Security